Veeam Backup & Replication Security Best Practice Guide
Why not in Production domain?
Microsoft Active Directory is the heart of the IT infrastructure for nearly every organization. When setting up the Veeam Availability infrastructure keep in mind the principle that a data protection system should not rely on the environment it is meant to protect in any way! This is because when your production environment goes down along with its domain controllers, it will impact your ability to perform actual restores due to the backup server’s dependency on those domain controllers for backup console authentication, DNS for name resolution, etc.
Furthermore, Production domains are the place where you have the higher number of users, thes the higher number of potention targets for social engineering or phishing. So production domains are to be considered more vulnerable. Once intruders get into the production domain they find a way to get high provileges. An intruder gaining high privileges on a VBR Server can get information about the infrastructure it protects. Getting this information allows for them to hit harder, potentially drive an attack that will have more impact, be more publicly visible, and longer to recover from.
Workgroup or Domain?
Microsoft Active Directory consists of Forests and Domains.
A forest is a collection of one or more Active Directory domains that share a common logical structure, directory schema (class and attribute definitions), directory configuration (site and replication information), and global catalog (forest-wide search capabilities). Domains in the same forest are automatically linked with two-way, transitive trust relationships.
A domain is a partition in an Active Directory Forest. Partitioning data enables organizations to replicate data only to where it is needed. In this way, the directory can scale globally over a network that has limited available bandwidth.
Security Domains Overview
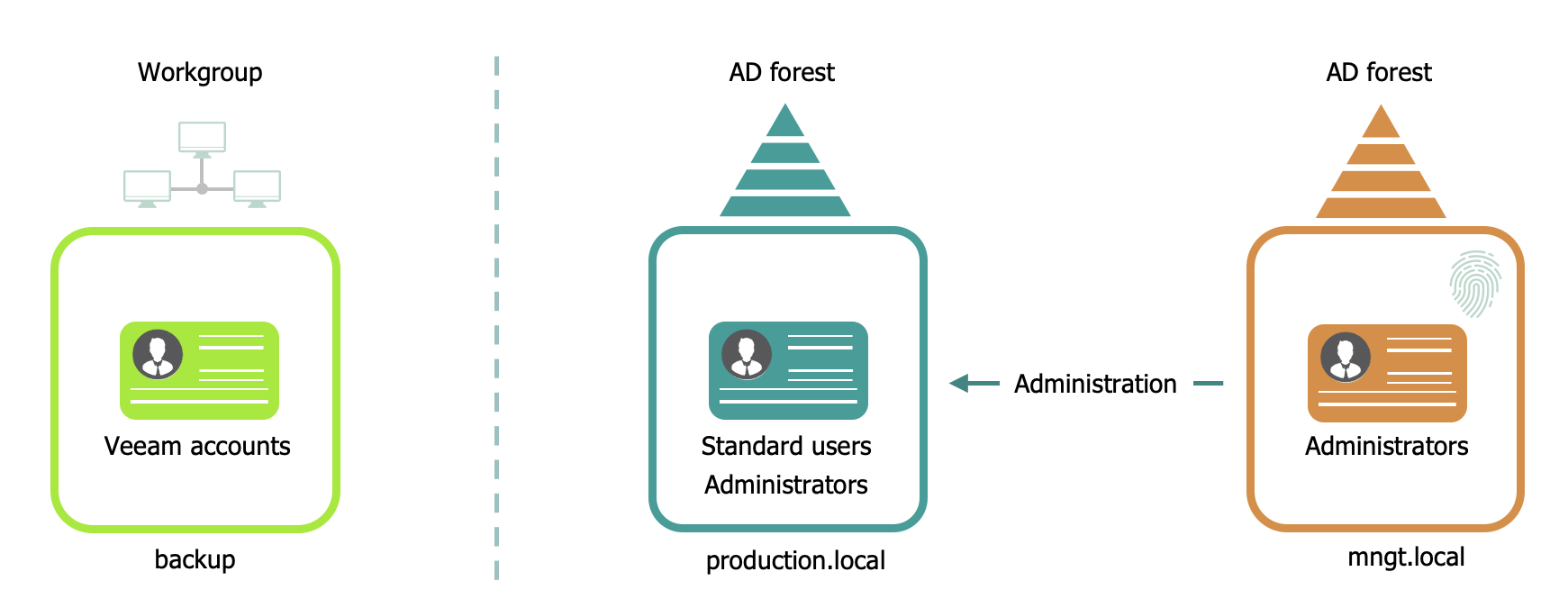
When securing administrative accounts and the Veeam Availability Infrastructure installation you have a few options from most secure to less secure:
- Add the Veeam components to a management domain that resides in a separate Active Directory Forest and protect the administrative accounts with two-factor authentication mechanics;
- Add the Veeam components to a separate workgroup and place the components on a separate network where applicable;
- Add the Veeam components to the production domain but make sure the accounts with administrative privileges are protected with two-factor authentication.
Best Practice
For the most secure deployment add the Veeam components to a management workgoup or a management domain that resides in a separate Active Directory Forest and protect the administrative accounts with two-factor authentication mechanics. This way the Veeam Availability Infrastructure does not rely on the environment it is meant to protect.
Windows Workgroup
When using a Workgroup, you will need to have everything carefully documented because of management and compliancy reasons. Every system needs to be configured independently per system with a local security policy, as well as users, permissions, etc. If you have multiple Veeam servers and users, this could become extremely cumbersome in larger environments. Also forget about Kerberos authentication with a workgroup server, you will be using NLTM instead.
Be aware though that a Workgroup is harder to defend against threats from the inside like a disgruntled employee because you will be using local accounts on the workgroup servers, and you cannot just switch off a single AD account locking out that specific employee from the critical infrastructure. Also, it is harder to prove for compliancy reasons that the systems are safe and being utilized as they should be. A Workgroup setup is a good solution for small environments.
Pros
- Fast and easy to setup
- Separates Veeam accounts from Domain privileged accounts (helps against keyloggers and breach of the production domain)
- Does not rely on the environment it is meant to protect
- No additional infrastructure servers required like: Domain Controllers, NTP and DNS
Cons
- Large management overhead in large(r) environments
- No Kerberos communication when logging into a standalone server (workgroup) only NTLM
- Harder to become compliant, do compliancy checks and proof to be compliant as an organization
- Impossible to use gMSA authentication system for guests backups interaction
Management Domain
While this approach does add a forest to an Active Directory environment, the cost and complexity are limited by the fixed design, small hardware/software footprint, and small number of users. Enabling central management of policies, user rights and permissions makes management easy. It also enables one-click deactivation of a single AD account when you face an inside threat. Setting up a separate Forest with a management domain is a great solution for large(r) environments. You can also add multi-factor authentication on the domain to protect the administrative accounts even further, blocking man in the middle attacks and key loggers.
Pros
- Easy to manage
- One-click deactivation of a single AD account
- Does not rely on the environment it is meant to protect
- Secure Kerberos communication between different Veeam components
- Use group polices to control the domain and fulfil compliancy easier
- Can integrate Multi-Factor Authentication (MFA) for extra layer of security
Cons
- Will need extra infrastructure components
- Needs more knowledge to set it up correctly
- Kerberos is condered more secure but is still vulnerable (See “kerberoast”)
What type of trust?
Forest trusts help you to manage a segmented Active Directory Domain Services (AD DS) infrastructure and support access to resources and other objects across multiple forests. Forests trusts are useful for companies seeking a solution for administrative autonomy. Using forest trusts, you can link two different forests to form a one-way or two-way transitive trust relationship. A forest trust allows administrators to connect two AD DS forests with a single trust relationship to provide a seamless authentication and authorization experience across the forests.
Trusts Overview
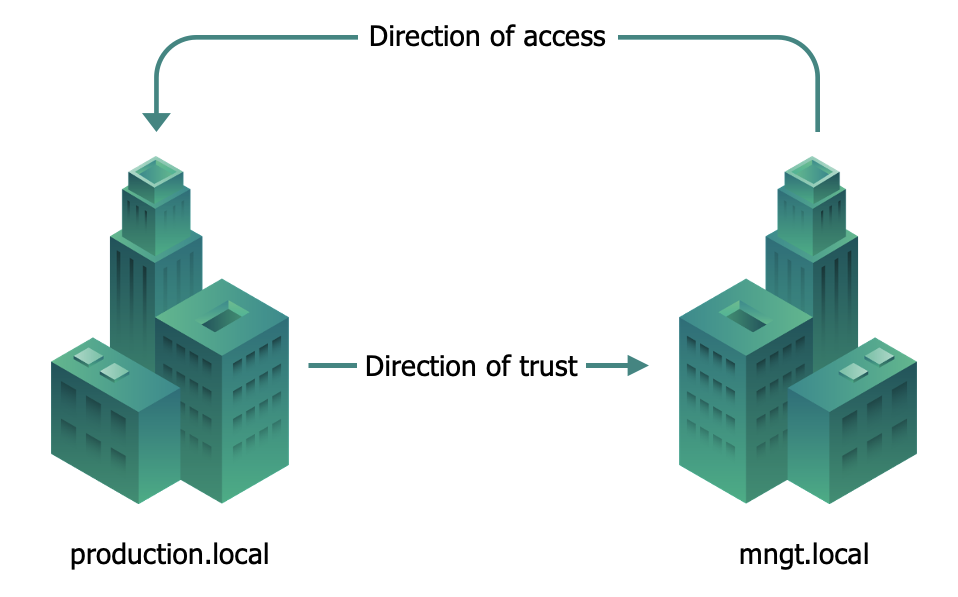
If a one-way forest trust is created between two forests, members of the trusted forest can utilize resources located in the trusting forest. However, the trust operates in only one direction. In this example you want the production domain to trust the management domain with a one-way forest trust. You will have an incoming one-way forest trust on the management domain.



