NIST Cybersecurity Framework Alignment
All the topics covered in the Design and implementation section can be mapped to the five functions of the NIST Cyber Security Framework.
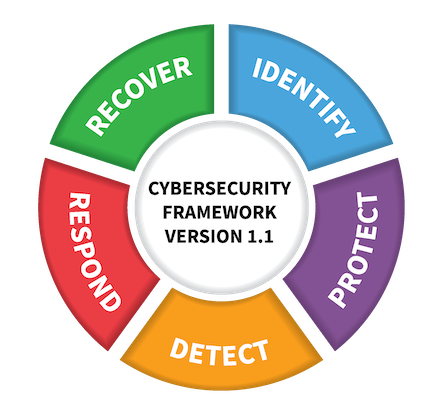
Identify
“Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs.”
Identification is mainly organisational and will consist for example in workloads categorisation, risk assessment, risk management. During the identification process, keep in mind identification aims:
- What may be targeted by attackers (Backups first in case it’s ransomware)
- What should be recovered first (foundation, main building, outbuildings)
Veeam helps to validate dependencies between assets (trial/error)
- Veeam Backup and replication SureBackup / SureReplica
- Veeam Disaster Recovery Orchestrator
Veeam provides post-identification tools to keep compliance
- Veeam One Business view, Tagging management
- Data Locality management
Protect
“Develop and implement appropriate safeguards to ensure delivery of critical services. The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event.”
Protection principles Protect Backups Protect Infrastructure Educate Staff
Physical security Role Based Access Controls on a physical level Screening Tailgating Surveillance Multi-factor authentication Equipment Racks Embedded electronic security
Roles and Users Anonymization Password management policy Lockout policy Required Permissions
Networking Authentication protocols Encryption in flight Segmentation
Repository Hardening Encryption at Rest Repository Specifics Windows Backup Repository WORM Storage with Veeam Hardened Repository
Hardening backup components and mechanisms Attack surface reduction Workgroup or Domain ? Application Processing
Detect
“The goal of the Detect function is to develop and implement appropriate activities to identify the occurrence of a cybersecurity event. The Detect Function enables timely discovery of cybersecurity events.”
Threat Detection Visibility Honeypot servers Honeypot users, also read Anonymization Veeam One alarms VMware visibility
Respond
“Develop and implement appropriate activities to take action regarding a detected cybersecurity incident. The Respond Function supports the ability to contain the impact of a potential cybersecurity incident.”
Physical Security incident response
Recover
“The goal of the Recover function is to develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. The Recover Function supports timely recovery to normal operations to reduce the impact from a cybersecurity incident.”
Have a recovery strategy in place
