Veeam Backup for Microsoft 365 Best Practices
Segmentation
Ultimately, all security is about protecting valuable assets - in this case, it is Data. However, that protection involves a defense-in-depth strategy that includes all layers. To implement defense-in-depth, identify the most valuable data and build layers of defense around it to protect its availability, integrity, and confidentiality.
AA zone is an area with a distinct characteristic, purpose, use, and/or subject to specific restrictions. Implementing zones is an effective strategy for mitigating various types of risks. By securing your environment more granularly and efficiently, you can also reduce associated costs. Rather than applying the same level of protection universally, you can associate systems and information with specific zones. As a result, systems subject to regulatory compliance can be grouped into subzones, limiting the scope of compliance checking and consequently reducing costs and the time needed for lengthy audit processes.
Consider the significance of the data and systems within each specific zone and determine who should have access to them. Communication is restricted to systems in adjacent zones. A typical data classification for a zone involves shared criteria such as availability, confidentiality, integrity, access controls, and requirements for auditing, logging, and monitoring.
These shared characteristics and requirements naturally result in a degree of isolation, occurring not only between zones but also within zones, referred to as subzones.
Reducing the attack surface of data and systems within a zone can be achieved by exposing only a limited number of services through the zone’s perimeter and implementing strict access controls to limit access to specific user groups. This approach requires a potential attacker to breach all outer zones before reaching the restricted zone containing critical data, thereby lowering the likelihood of data theft or mutilation. Additionally, this strategy enhances the availability of critical systems.
Using a zone model as a strategic defense model for Veeam components involves adhering to key principles and rules during the design phase:
- Secure by Design
- Know what is important to secure and rank it
- Know your attack vectors and possible ways to secure them
- Use the principle of least privilege
- Have insight into costs and benefits
Important: The importance of security cannot be overstated, and it’s crucial to recognize that there’s no one-size-fits-all solution. Achieving security requires a continuous and vigilant approach. It’s not just about following best practices; it involves understanding your organization’s specific needs and considering factors like budget, risks, and potential outcomes. Regular assessment, adaptation, and staying informed are essential for maintaining a robust security posture.
Layers between zones
The cybersecurity layers approach aligns well with Veeam’s common practices in establishing a comprehensive security strategy. Here’s a summary of each layer:
- Human Layer: Focuses on human-centric aspects, including training and awareness programs, as well as physical access controls.
- Perimeter: Involves technologies and measures at the network perimeter, such as firewalls, spam filters, and intrusion detection/prevention systems.
- Network: Encompasses secure network design, VLANs (Virtual Local Area Networks), and multi-layer firewalls and switches.
- Endpoint: Addresses security measures at individual endpoints, including antivirus software, software firewalls, and breach detection agents.
- Application: Involves strategies like patching and updates to secure applications against vulnerabilities.
- Data: Emphasizes encryption for data, both at rest and in motion, to protect sensitive information.
- Mission Critical: Ensures the security of mission-critical elements, including robust backup systems and a well-defined response and recovery plan.
By considering security across these layers, you can create a more resilient defense against a wide range of cyber threats. Each layer plays a crucial role in the overall cybersecurity posture, and a comprehensive approach is essential for mitigating risks effectively.
Example using Zones
Your emphasis on implementing zones and highlighting the significance of threat visibility is crucial in contemporary cybersecurity practices. Segmenting the infrastructure into zones offers several advantages, including enhanced control, reduced attack surface, and improved detection capabilities. By categorizing components based on their importance and functionalities, organizations can tailor security measures to specific needs.
Furthermore, recognizing the internal threat landscape underscores the importance of insider threat detection and prevention mechanisms. Implementing robust access controls, monitoring user activities, and employing behavior analytics can contribute to early threat detection and response.
In the context of hardening Veeam Backup for Microsoft 365 infrastructure, logical zoning provides a structured approach to security, aligning with the principle of least privilege and promoting a defense-in-depth strategy. This proactive stance is instrumental in securing critical data and systems from both internal and external threat.
Identifying management accounts and components as high-value targets aligns with attackers’ common strategy. In the context of Veeam Backup & Replication, securing access to these components is crucial. Robust access controls, multi-factor authentication, and continuous monitoring are essential for preventing unauthorized manipulation and ensuring the integrity of backup and recovery processes. Regular security assessments and audits help identify and address potential vulnerabilities in this critical area.
Let’s categorize the major Veeam Availability components into designated zones:
- Veeam Backup for Microsoft 365 Console, also known as Console.
- Veeam Backup for Microsoft 365 Server, the core component orchestrating various jobs and managing data flow through the infrastructure.
- The Veeam Backup for Microsoft 365 Restore Portal, facilitated by the RestAPI service, which might require inbound internet access.
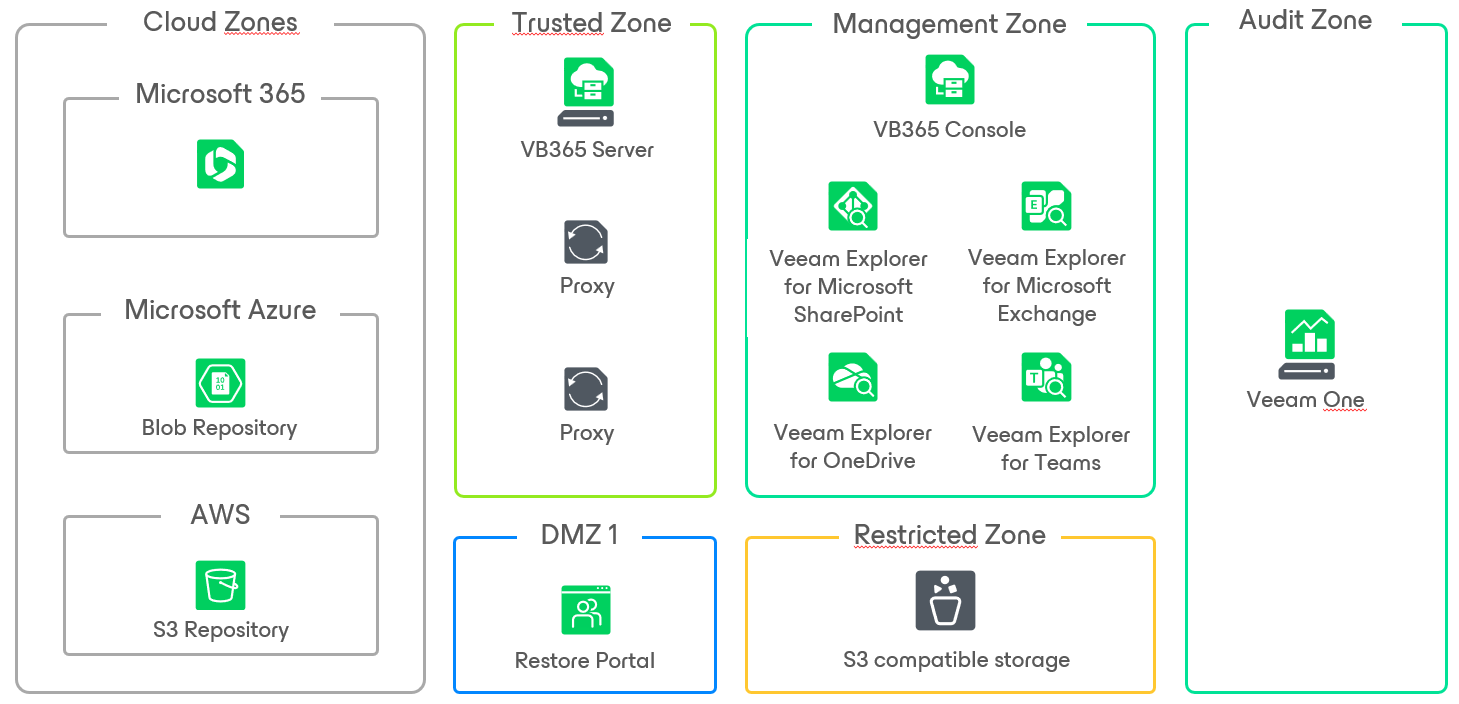
Management Zone
In the management zone, infrastructure services such as DNS, Active Directory, and SMTP are positioned. This zone may also include the VMware vCenter server and/or Microsoft System Center Virtual Machine Manager (SCVMM). In terms of Veeam components, the Veeam Backup for Microsoft 365 Server resides in this Management zone. This server orchestrates all jobs and updates various Veeam components across different zones from a central location.
Trusted Zone
The Veeam Backup for Microsoft 365 Server resides in the Trusted Zone, where it orchestrates backup jobs and manages Proxies, also situated within this zone. The Trusted Zone necessitates secure and controlled internet access for utilizing Microsoft 365 APIs, cloud repository APIs, and downloading updates for various components in the infrastructure. These systems within the Trusted Zone require efficient internet connectivity to Microsoft cloud services.
Restricted Zone
Primary storage, housing backup data, and other components storing data should be positioned in this restricted zone. Access to this zone must be restricted, allowing only backup infrastructure components and administrators with strict rights. Direct access by any user should be prohibited.
DMZ
The DMZ accommodates systems requiring exposure to the untrusted zone, This zone proxies access between systems in the DMZ and the Trusted Zone. Within this zone, the Veeam Backup for Microsoft 365 Restore Portal is located, providing end-user access for self-service restores. To enhance security, employing technologies such as a reverse proxy is recommended to publish the Restore Portal for public use. An example of creating an open-source reverse proxy can be found on Jorge de la Cruz’s blog pages
Audit Zone
Visibility is crucial for protecting, detecting, and promptly containing threats. In the Audit Zone, monitoring solutions such as Veeam ONE, IDS, and IPS systems should be positioned to enhance oversight and surveillance.
Firewall Ports
It is recommended to restrict open ports to only essential services in each zone. The latest list of ports for all services and APIs can be found in the Helpcenter User Guide.



