Veeam Backup for Microsoft 365 Best Practices
Workgroup or Domain ?
Microsoft Active serves as the core of the IT infrastructure for nearly every organization. When establishing the Veeam infrastructure, it’s crucial to adhere to the principle that a data protection system should operate independently of the environment it is designed to safeguard. This is imperative because if your production environment, along with its domain controllers, experiences downtime, it will impact your ability to perform restores. The backup server relies on these domain controllers for authentication, DNS for name resolution, and more.
Microsoft Active Directory consists of Forests and Domains.
A forest is a collection of one or more Active Directory domains that share a common logical structure, directory schema (class and attribute definitions), directory configuration (site and replication information), and global catalog (forest-wide search capabilities). Domains in the same forest are automatically linked with two-way, transitive trust relationships.
A domain is a partition in an Active Directory Forest. Partitioning data enables organizations to replicate data only to where it is needed. In this way, the directory can scale globally over a network that has limited available bandwidth.
Security Domains Overview
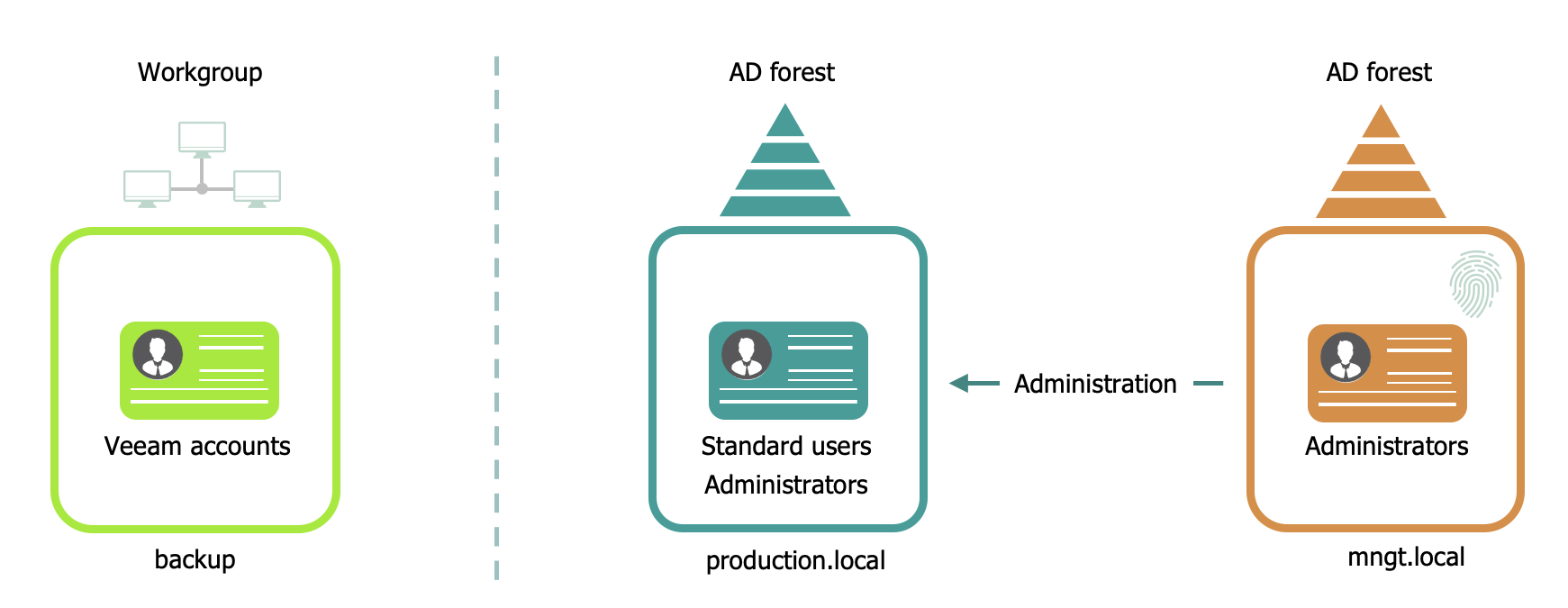
When securing administrative accounts and the Veeam infrastructure installation you have several options ranked from most secure to less secure:
- Management Domain in Separate Active Directory Forest:
- Add the Veeam components to a management domain residing in a separate Active Directory Forest.
- Protect administrative accounts with two-factor authentication mechanics.
- Separate Workgroup and Network:
- Add the Veeam components to a separate workgroup.
- Place the components on a separate network where applicable.
- Production Domain with Two-Factor Authentication:
- Add the Veeam components to the production domain.
- Ensure accounts with administrative privileges are protected with two-factor authentication.
Best Practice
For the most secure deployment add the Veeam components to a management domain that resides in a separate Active Directory Forest. Additionally, protect the administrative accounts with two-factor authentication mechanics.
Windows Workgroup
When using a Workgroup, precise documentation becomes crucial due to management and compliance requirements. Each system needs individual configuration with a local security policy, user settings, permissions, etc. In larger environments with multiple Veeam servers and users, this can become challenging. Additionally, forget about Kerberos authentication with a Workgroup server; NLTM will be used instead.
Be aware that a Workgroup is more challenging to defend against internal threats, such as a disgruntled employee, because local accounts are used on the workgroup servers. You cannot easily disable a single AD account to lock out that specific employee from the critical infrastructure. Additionally, it is more difficult to demonstrate compliance with safety and proper utilization of systems for compliance reasons. A Workgroup setup is a suitable solution for small environments.
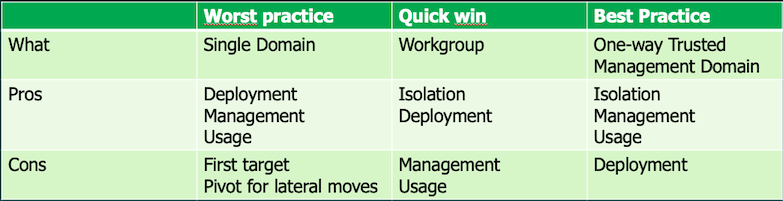
Pros
- Fast and easy to setup
- Separates Veeam accounts from Domain privileged accounts (mitigates keylogger risks and breaches of the production domain)
- Does not rely on the environment it is meant to protect
- No additional infrastructure servers required, such as Domain Controllers, NTP and DNS
Cons
- Hign management overhead in large(r) environments
- No Kerberos communication when logging into a standalone server (workgroup) only NTLM
- More challenging to achieve compliance, conduct compliance checks, and prove compliance as an organization.
- Impossible to use gMSA authentication system for guests backups interaction
Management Domain
While this approach does add a forest to an Active Directory environment, the cost and complexity are mitigated by the fixed design, small hardware/software footprint, and small number of users. Centralized management of policies, user rights, and permissions facilitates easy administration. It also allows for one-click deactivation of a single AD account in the event of an internal threat. Establishing a separate forest with a management domain is an excellent solution for larger environments. Additionally, you can implement multi-factor authentication on the domain to enhance the security of administrative accounts, preventing man-in-the-middle attacks and keyloggers.
Pros
- Easy to manage
- One-click deactivation of a single AD account
- Does not rely on the environment it is meant to protect
- Secure Kerberos communication between different Veeam components
- Utilize group policies to control the domain and facilitate compliance more easily.
- Can integrate Multi-Factor Authentication (MFA) for an extra layer of security.
Cons
- Requires additional infrastructure components.
- Requires more knowledge to set it up correctly.



