Veeam Backup & Replication Best Practice Guide
SureBackup overview
SureBackup® allows for verification of regular image-based backups and can operate in two different ways:
- Content Scan for malware or any data, based on antivirus software and/or YARA rules
- Full recoverability (live) testing
To perform Content Scan only, the image is mounted and scanned, and an optional integrity check can be run. No application group nor virtual lab is needed in that case.
To perform live testing of guests, SureBackup® will isolate live images from the rest of the production environment and run pre-defined tests against them, as described in below illustration. Content Scan can be run in addition in the same SureBackup® job.
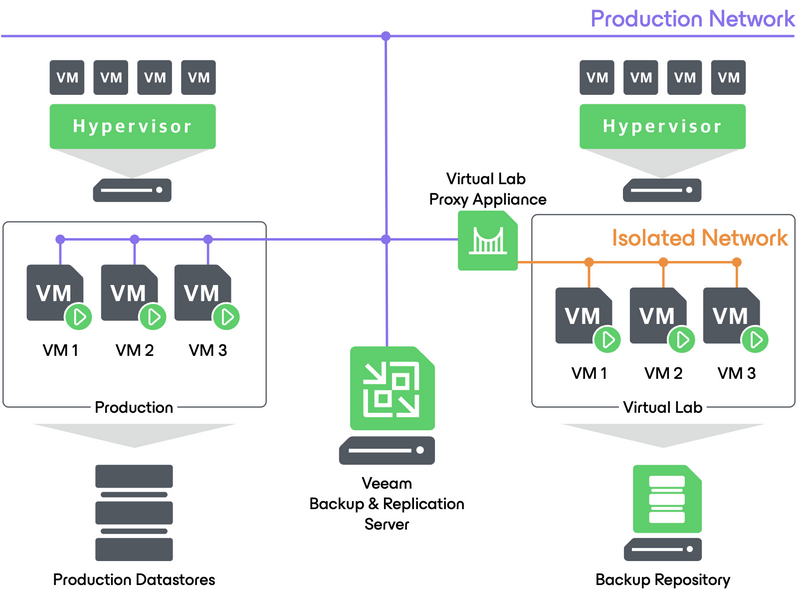
This is made possible using different Veeam features such as Virtual Lab, Instant VM Recovery® and application groups in conjunction with specific testing scenario.
Infrastructure concerns
SureBackup is relying on Veeam Instant VM Recovery feature. This means that the repository must offer enough performance to concurently start as many concurrent IVMR sessions as configured in the SureBackup job and the application group.
For example, if a SureBackup job is configured to test three VMs in parallel and an application group is configured with two VMs, then the repository must offer enough IOPS to run five VMs at the same time.
Before configuring SureBackup jobs, it is recommended to run Instant VM Recovery sessions to test the repository and make sure it will sustain the desired load.
Configuring virtual labs
To enable testing of a guest image (could be a simple ping test on the network interface), the virtual lab proxy appliance will be deployed.
Configuring virtual lab networking
To provide the isolated environment to start and test backup images, the virtual lab will deploy a virtual switch (or use a predefined Distributed virtual switch if it is configured to run on multiple hosts), create necessary port groups and deploy the vLab appliance.
Note: it is strongly advised to keep the virtual lab appliance external network on the network where the Veeam Backup & Replication server resides. If for any reason this is not possible routing rules should be added in the production network to access the guests images booted inside the virtual lab. The static routing added to the Veeam Backup & Replication server itself will not be propagated to the network equipment.
Virtual lab appliance networking
The key point of virtual lab networking is the Network Address Translation rules mechanisms used by the vLab appliance. Depending on the chosen configuration type the deployed items and configuration will differ.
Basic-Single host configuration
No special input is requested. A virtual switch is deployed on the designated host and the corresponding port group is created with the same VLAN ID than the production port group. Standard vSwitch automatically deployed as part of the virtual lab The vLab appliance VNIC residing inside the virtual lab private network will be automatically setup and a corresponding NAT rule will be created.
Note: Basic-Single host configuration requires that backup server and VMs to test are connected to the same network. As the backup server should always be in a different network than production for security reasons, please use Advanced Single-Host Virtual labs.
Advanced-Single host configuration
This configuration mode will allow manual configuration of every component and networking rules. When selected new configuration tabs will appear in the wizard. This is the most commonly used configuration mode.
Isolated networks
Each production network with unique settings used in production by verified VM should be mirrored inside the virtual lab through the isolated network settings.
Network settings
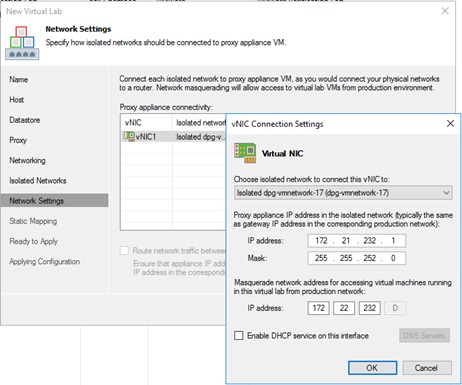
The gateway IP address of the production networks should be used on the vNics allowing the vLab appliance to act as a gateway for the isolated guests without reconfiguring them.
In the following illustration the production network gateway address 172.21.232.1 is assigned to the corresponding vNic of the virtual lab appliance.
Masquerading
This parameter will allow accessing the tested guests through the vLab appliance by creating a static route on the Veeam Backup & Replication server at virtual lab start-up. For example, if production guest IP is 172.21.233.20, then the masquerade IP could be 172.22.233.20.
Note: It is recommended that virtual lab proxy appliance and backup server are in the same network. If the backup server and virtual lab proxy appliance are in different networks, then the masquerade IP range must not be already in use on the production network.
Corresponding routes will be automatically created on the Veeam Backup & Replication server when the SureBackup job starts. These temporary routes will be used to perform network related tests and to access the VM from the Veeam Backup Server. Once the SureBackup job is complete these routes will be deleted.
Network routing between vNic
This option has to be selected when the vLab appliance is acting as the router between multiple isolated networks. The vLab appliance will then act as the network gateway between all isolated networks.
Advanced-Multi host configuration
This type of configuration is commonly used for SureReplica jobs, or sometimes when mixing SureBackup and SureReplica. The common concern is to allow tested guests images to reside on multiple hosts which then necessitates the use of a predefined DVS (Distributed Virtual switch).
Whenever Multi host configuration shall be used, special attention should be paid to distributed virtual switch VLANs configuration, as the VLAN IDs configured for the virtual lab should be unique and must be tagged on the network equipment.
Note: if for some reason the VLAN ID configured is already in use on the production environment, the Virtual Lab will not be isolated from the production environment, causing severe networking issues, such as duplicate IPs or Mac Addresses.



