Veeam Service Providers Best Practice Site
Authentication and authorization
This section contains settings regarding authentication and authorization that you must consider when deploying the VSPC.
- Portal Users & Administrators
- Multi-Factor Authentication (MFA)
- Single Sign-On Authentication (SSO)
1. Portal Users & Administrators
By default, the only user that can access the Administrator Portal on behalf of a Service Provider is the Portal Administrator. VSPC grants this role to members of the Local Administrators user group on the machine where the VSPC Server component is installed. It is highly recommended to change this and instead make use of dedicated Active Directory security groups.
1.1 Create a dedicated Portal Administrator group.
-
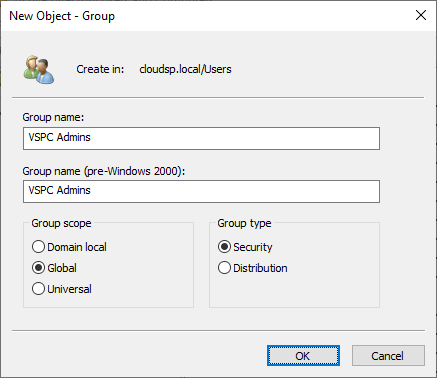
In Active Directory Users and Groups create a new group called VSPC Admins.
-
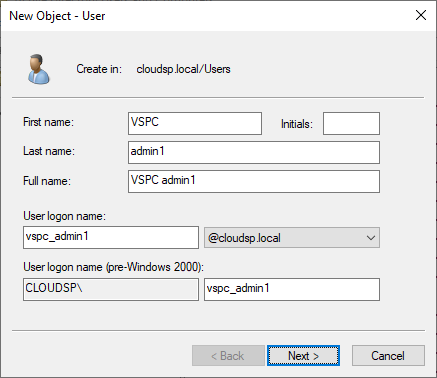
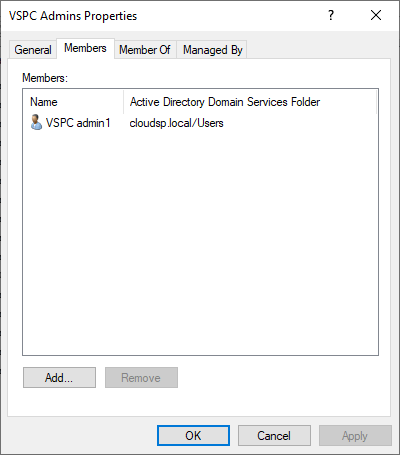
Also in Active Directory Users and Groups, create a dedicated user account for each Administrator that requires access to the VSPC and add it to the AD security group we just created.
-
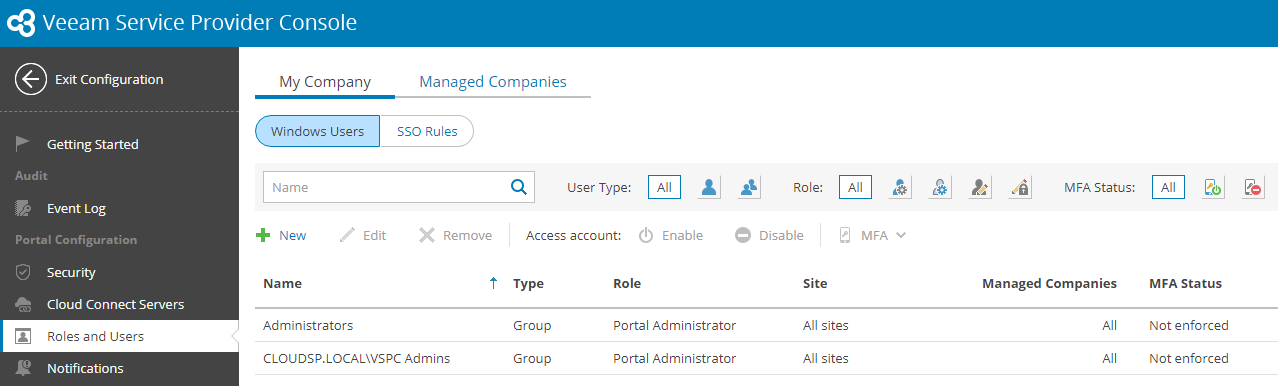
Login to VSPC using the Windows Local Administrator account and go to Configuration -> Roles and Users.
Under My Company select Windows Users and click New to enter the wizard. -
At the Account step look for the VSPC Admins group.
Select the group and Click Next.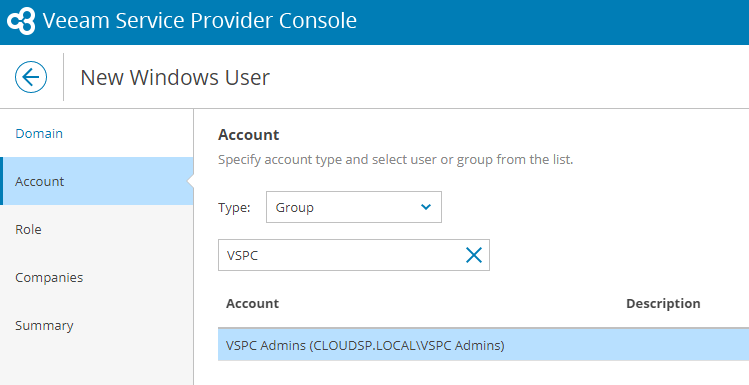
-
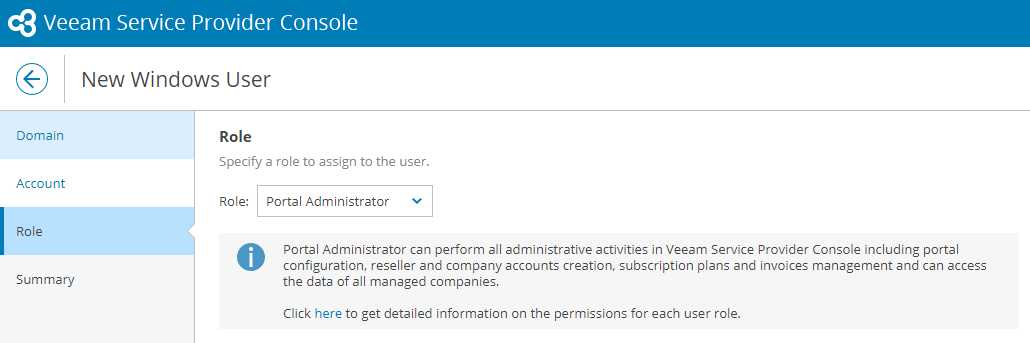
At the Role step click in the dropdown list and select Portal Administrator. Click Next.
-
Click Finish to add the AD group.
-
To be able to log in to the VSPC Web UI, users or groups must be specified in the Allow log on locally security policy setting on the machine where the VSPC Server component is installed.
Go to Start Menu -> Run -> type secpol.msc to open the Local Security Policy.
Under Local Policies -> User Rights Assignment edit the Allow to log on locally properties and add the AD security group with the Portal Administrators.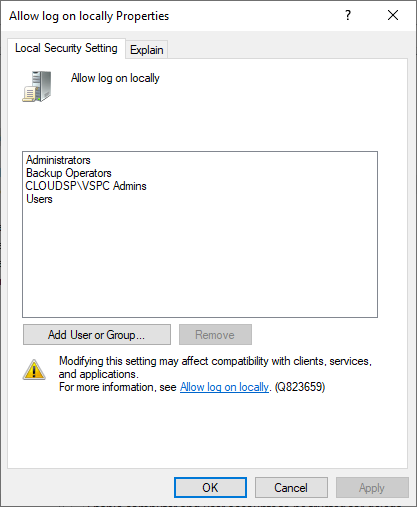
-
Now you can go back to the console url and login using the DOMAIN\USER format.
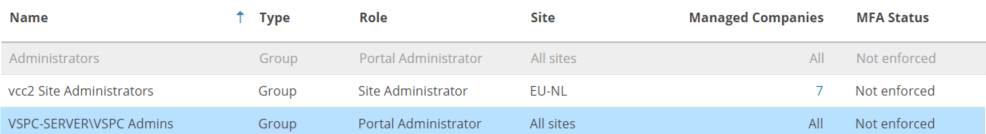
1.2 Disable the predefined Administrators group.
By default, contains a predefined Administrators group that cannot be removed nor disabled. This is in fact the Local administrators group of the VSPC server itself and is there to prevent a complete lock-out from the backup portal.
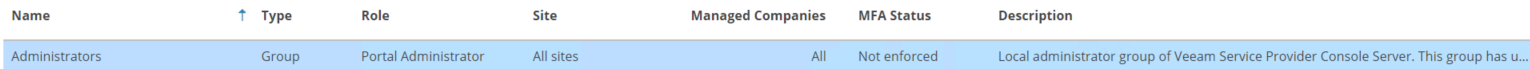
Note: When you have added at least one Cloud Connect server, there will also be a VCC Site Administrators group which can be easily disabled. This predefined group has only Site Administrator permissions.
However when you add the VSPC server to the domain, you might have other users and groups added to the Local Administrators group such as Domain Admins. It means that these users are also able to log into the VSPC backup portal.
To tighten security we can create a dedicated local group onto the VSPC server and only allow these users access:
- Create a local group onto the VSPC server and add the required Active Directory users/groups in there.
- In VSPC, under Roles & Users, add the newly created local group and give it the Portal Administrator role.
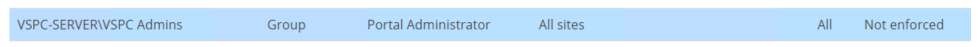
Then follow the steps below to disable the predefined group:
- Open the following config file on the VSPC Server.
v7: C:\Program Files\Veeam\Availability Console\ApplicationServer\Veeam.MBP.Service.exe.config v8.x: C:\ProgramData\Veeam\Veeam Availability Console\Configuration\Service\configuration.overrides.json - Set the following key value to True:
v7: Find the *AuthenticationSettings* section. Set "isDisablingDefaultLocalAdminGroupEnabled" to "True" v8.x: "Authentication_IsDisablingDefaultLocalAdminGroupEnabled": "True" - Restart the Veeam Management Portal Service or restart the entire VSPC Server machine.
- Now you are able to disable the predefined group.
2. Multi-Factor Authentication (MFA)
For additional security of user accounts, it highly recommended to enable MFA. By default it’s up to the user on whether to configure MFA for the account or not, however MFA can also be enforced by the portal administrator. It is a best practice to enforce MFA for all users and groups with the Portal Administrator role.
If you configure MFA for an account that is used for API integration, make sure to first configure an API key or the integration will stop working.
Guide: Configuring Multi-Factor authentication
3. Single Sign-On Authentication (SSO)
VSPC supports SSO authentication based on the SAML 2.0 protocol. This way service providers and resellers (from within the VSPC) can leverage their existing SSO service in order to not work with local users or yet another user domain. Administrators, resellers and end-users can access the VSPC without the need to provide credentials.
Guide: Configuring SSO authentication
SSO configuration examples:



