Domain or workgroup
From a security perspective all related components can be deployed in a workgroup or a domain.
The best practice is to use a separate domain. However, when using them in a workgroup the following settings are required:
- The Remote Registry service must run on the target machine. The service startup type must be set to Automatic.
Security zones
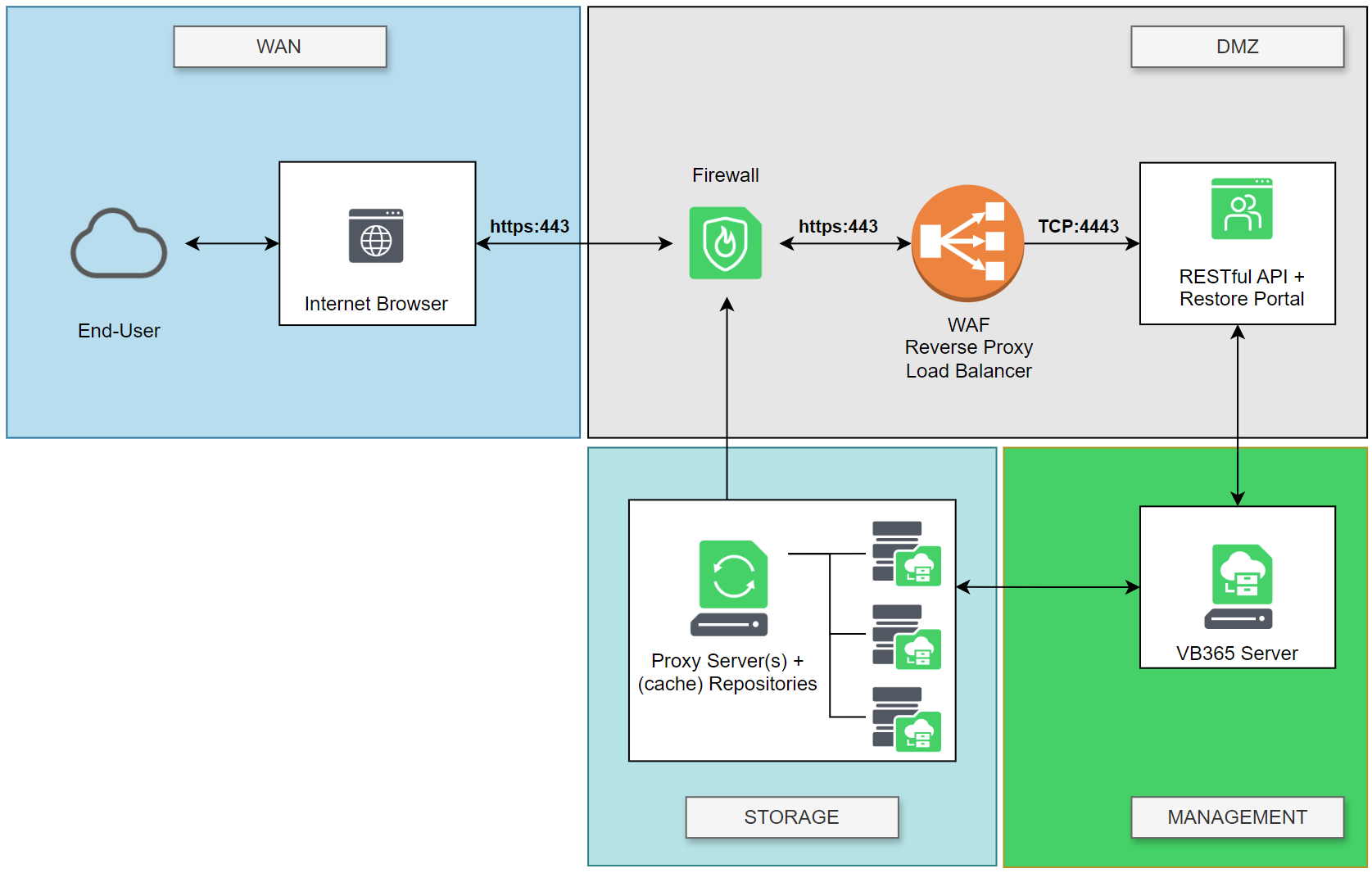
The different components should be put within the following zones (networks):
- WAN
- Public Cloud Object Storage
- DMZ
- VB365 API/Portal server
- VB365 Console
- VB365 Explorers
- MANAGEMENT
- VB365 Controller
- STORAGE
- VB365 Proxy server(s)
- On-premises Object Storage
This deployment can be further enhanced by:
-
Putting a Web Application Firewall (WAF) in front of the API/Portal server. This can provide additional advantages, but not limited to:
- A WAF is a type of reverse proxy that protects the API/Portal server from exposure by having clients pass through the WAF before reaching the API/Portal server.
- Set policies to protect against vulnerabilities in the application by filtering out malicious traffic.
- DDoS attack protection (e.g. rate limiting).
-
Putting a Reverse Proxy Server in front of the API/Portal server. This can provide additional advantages, but not limited to:
- Protect the API/Portal server from exposure by having clients pass through the Reverse Proxy Server before reaching the API/Portal server.
- SSL/TSL certificates offloading (if applicable).
- Certificate management and rotation.
-
Putting a Load Balancer in front of the API/Portal server. This can provide the same benefits as a reverse proxy including:
- Load balancing between multiple API/Portal servers when deployed for high-availability of the service.
The following diagram represents an example of the different security zones for the entire solution stack:
Certificates
In VB365, certificates are heavily used between all different components as well as the Microsoft 365 cloud. Please check the Certificates Overview page for more details.
Encryption
NATS
By default, the NATS server that you deploy along with VB365 on the target machine does not use the TLS encryption. To enhance security of the NATS server, we recommend that you enable TLS encryption for the NATS server traffic.
Backup data
- Backup data is automatically encrypted in-flight between Backup Proxies and Object Storage Repositories.
- Backup data is stored encrypted at-rest in Object Storage Repositories using an encryption password specified by the administrator.
- Use separate encryption passwords for each Object Storage Repository. When a client decides to leave the service, you can hand over the encryption password without compromising any other repositories.
- Backup data is not encrypted at-rest for the following types of backup repositories:
- A local directory on a backup proxy server.
- Direct Attached Storage (DAS) connected to the backup proxy server.
- Storage Area Network (SAN).
- Network Attached Storage (SMB shares version 3.0 or later).
- Do not use 3rd party encryption software for backups in backup repositories as this may lead to unpredictable system behavior and inevitable data loss. Only use encryption that is transparent such as Bitlocker.
- Do not use deduplication software or deduplication appliances for JetDB-backed repositories. This is not supported.
- More info on the data encryption standards, algorithms and keys used can be found in the User Guide.
